--Online Distance Learning Assignments and Information--
Coach Burrill's Class Syllabus
AP CS Principles Syllabus

AP Test Information
Section I: End-of-Course Multiple-Choice Exam- Wednesday May 15th, 2024 at 12pm in the WR Gym.
70 Multiple-Choice Questions | 120 Minutes | 70% of Score | 4 answer options
57 single-select multiple-choice
5 single-select with reading passage about a computing innovation
8 multiple-select multiple-choice: select 2 answers
Section II: Create Performance Task- Project Due Tuesday April 30, 8:59pm PST.
30% of Score
Students will develop a computer program of their choice. Students need at least 12 hours of in-class time to complete.
AP Computer Science Principles Period Information
Period 2 |
Period 4 |
Period 6 |
Code.org Class Code-
VYSJML |
Code.org Class Code-
NTNSXV |
Code.org Class Code-
RHZYVV |
AP Test Class Code-
RGMGGP |
AP Test Class Code-
DA3EVD |
AP Test Class Code-
4V6EXR |
Week 18 |

Day 40- Monday December 11-
- Final Review Game
- Good luck on all your finals!
|
Week 17 |

Day 38- Tuesday December 5-

Day 39- Thursday December 7-
|
Week 16 |

Day 35- Monday November 27- Unit 5 Building Apps- Lesson 4 Controlling Memory with Variables
Payoff- Great Snickers Bet of 2023
-
Students will be able to:
- Use variables in a program to store numeric values.
- Store the value returned by a function (randomNumber, promptNum) in a variable for use in a program.
- Debug problems related to variable re-assignment.
- Write arithmetic expressions that involve variables.
- Reason about multi-line segments of code in which variables are re-assigned multiple times.
- Video- Intorduction to Variables- Part 1 (4min)
- Video- Intorduction to Variables- Part 2 (3min)
- New Vocab and Commands-
- Key Takeaways
- Numbers and strings are two different types of values
- Expressions evaluate to a single new value
- When variables are in the expression just make a copy, don’t change the actual variable.
- Variables are “assigned” a new value
- Evaluate first, then assign
- Old values are deleted forever.
- Assignment just moves information around. It does not “connect” variables.
- Complete Unit 5 Lesson 4 (3pts)- As always, work with others.
Day 36- Wednesday November 29- Unit 5 - Lesson 5 Building an App: Clicker Game
-
Students will be able to:
- Use global variables to track numeric data in an app.
- Give a high-level explanation of what “variable scope” means.
- Debug problems related to variable scoping issues.
- Modify existing programs to add and update variables to track information.
- Create a multi screen "clicker" game from scratch
- New Vocab and Commands-
- == - The equality operator (sometimes read: "equal equal") is used to compare two values, and returns a Boolean (true/false). Avoid confusion with the assignment operator "=",
- Global Variable - A variable whose scope is "global" to the program, it can be used and updated by any part of the code. Its global scope is typically derived from the variable being declared (created) outside of any function, object, or method.
- If-Statement - The common programming structure that implements "conditional statements".
- Local Variable - A variable with local scope is one that can only be seen, used and updated by code within the same scope. Typically this means the variable was declared (created) inside a function -- includes function parameter variables.
- Variable Scope - dictates what portions of the code can "see" or use a variable, typically derived from where the variable was first created. (See Global v. Local)
- setText(id, text)
- if( ){ //code }
- __ == __
- Activity Guide - The Clicker Game (5pts)- Can turn in (Groups 1-3 Allowed), Must Grade Another Group
- Complete Unit 5 Lesson 5 (3pts)- As always, work with others.
- We will work on Clicker Game App on Monday December 2 when we get back from Thanksgiving Break. You will present at the end of class. (10pts)

Day 37- Thursday November 16- Unit 5 - Lessons 2 & 3 Building Apps
Finish Unit 5 Lessons 4 & 5- Finish Clicker Game App and Activity Guide, Must Grade Another Group and record results on Activity Guide.
Unit 5 Programming Test on Tuesday (25pts)
|
Week 15 |

Day 33- Tuesday November 14- Unit 5 Building Apps
- Share Group Drawings
- Great Snickers Bet of 2023
- Year 17-18, Unit 5, Lessons 1- Buttons and Events
- Students will be able to:
- Use Design Mode to user interface (UI) elements to a screen.
- Create a simple event-driven program by creating user-interface elements with unique IDs and attaching event handlers to them.
- Recognize debugging and responding to error messages as an important step in developing a program.
- Debug simple issues related to event-driven programming
- Video- Intro to Design Mode in App Lab (6 min)
- New Vocab and Commands-
- User Interface (UI) - The "User Interface" or UI of an app refers to how a person (user) interacts with the computer or app.
- UI Elements or objects, like buttons, images, text boxes, pull down menus, screens and so on.
- UI Events or controls, like click, scroll, move mouse, type keyboard key, etc.
- Event-driven program - a program designed to run blocks of code or functions in response to specified events (e.g. a mouse click)
- Event handling - an overarching term for the coding tasks involved in making your app respond to events by triggering functions.
- Event listener - a command (onEvent in App Lab) that can be set up to trigger a function when a particular type of event occurs on a particular UI element.
- Callback function - a function specified as part of an event listener; it is written by the programmer but called by the system as the result of an event trigger.
- event handling with onEvent
- Event Driven Programming Patterns
- App Lab Stuff-
- App Lab makes webpages in the language JavaScript
- HTML- Hyper Text Markup Language
- CSS- Cascading Style Sheets
- Complete 17-18, Unit 5 Lesson 1- No Need to Do Section 23 (3 Pts)
Great Snickers Bet of 2023
Day 34- Thursday November 16- Unit 5 - Lessons 2 & 3 Building Apps
Year 17-18, Unit 5, Lessons 2- Multi-screen Apps
- Students will be able to:
- Write a simple event-driven program that has multiple screens.
- Recognize debugging as an important step in developing a program.
- Use console.log to debug simple issues related to event-driven programming.
- New Vocab and Commands-
- Debugging - Finding and fixing problems in your code or algorithm
- User Interface (UI) - The "User Interface" or UI of an app refers to how a person (user) interacts with the computer or app.
- Event-driven program - a program designed to run blocks of code or functions in response to specified events (e.g. a mouse click)
- Event handling - an overarching term for the coding tasks involved in making your app respond to events by triggering functions.
- Using console.log
- Adding new screens and using setScreen
- Complete 17-18, Unit 5 Lesson 2 (3 Pts)
Year 17-18, Unit 5, Lessons 3- Building Multi-screen Apps
- Students will be able to:
- Develop and design a plan for multi-screen application
- Collaborate with a "thought partner" during the implementation of a project
- Create a multi-screen application in App Lab using simple UI elements and event handling
- New Vocab and Commands-
- Event-driven program - a program designed to run blocks of code or functions in response to specified events (e.g. a mouse click)
- Event handling - an overarching term for the coding tasks involved in making a program respond to events by triggering functions.
- Complete 17-18, Unit 5 Lesson 3 (3 Pts)
- Complete Activity Guide- Multi-screen App (3 pts) May complete Activity Guide and Multi Screen App (section 4) with 1-3 people in a group.
Have a great Thanksgiving Break and Beat the bRuins!
Great Snickers Bet of 2023
|
Week 14 |

Day 31- Tuesday November 7- Unit 3 Project- 20pts

Day 32- Thursday November 9-Unit 3 - Finish and Present Turtle Programming Project
|
Week 13 |
Day 28- Monday October 30- Unit 3 - Intro to Programming ('17-'18)
Complete Lesson 6- On own or with a friend
- Functions and Top-Down Design
Complete Lesson 7- On own or with a friend
- APIs and Function Parameters
- New Blocks
Lesson 6 & 7 Vocab-
- Efficiency: Can many severl deifferent things-
- It could mean the total number of primitive operations performed by the turtle.
- It could mean number of lines of code.
- It could hinge on the ability to reuse code within your own code.
- It could be about the speed and clarity with which you can write the program.
- Abstraction: a simplified representation of something more complex. Abstractions allow you to hide details to help you manage complexity, focus on relevant concepts, and reason about problems at a higher level.
- Function: a named group of programming instructions. Functions are reusable abstractions that reduce the complexity of writing and maintaining programs
- Top Down Design - a problem solving approach (also known as stepwise design) in which you break down a system to gain insight into the sub-systems that make it up.
- API - a collection of commands made available to a programmer
- Documentation - a description of the behavior of a command, function, library, API, etc.
- Hexadecimal - A base-16 number system that uses sixteen distinct symbols 0-9 and A-F to represent numbers from 0 to 15.
- Library - a collection of commands / functions, typically with a shared purpose
- Parameter - An extra piece of information that you pass to the function to customize it for a specific need.
- A "Comment" block doesn't do anything when you run the code. It is simply a way to leave notes in code. Programmers write comments into their code for two main reasons:
- sharing code with other programmers
- remembering their own thoughts or plans for code they write.
Day 29- Wednesday November 1-Unit 3 - Intro to Programming ('17-'18)
Complete Lesson 8- Creating Functions with Parameters
- Identify situations for creating functions with parameters.
- Incorporate functions with parameters into an “Under the Sea” digital scene.
- Test functions with parameters using random input.
- New Blocks-
Day 30- Friday November 3-Unit 3 - Intro to Programming ('17-'18)
Complete Lesson 9- Looping and Random Numbers
- Introduction to the for loop.
- Practice using loops to draw figures.
- Use loops in conjunction with Top-Down Design and random values to complete a digital scene.
Vocab-
- Loop: a programming construct that repeats a group of commands.
- Iteration: "loop" by another name - the repetition of a statement, process, or procedure.
- For Loop - A particular kind of looping construct provided in many languages. Typically, a for loop defines a counting variable that is checked and incremented on each iteration in order to loop a specific number of times.
Have Lessons 3-9 Complete by start of class onTuesday next week. 6pts.
|
Week 12 |
Day 26- Tuesday October 24- Finish Moneyball

Day 27- Thursday October 26- Turtle Programming
Code.org 2017-18, Unit 3, Lessons 3-5
Moneyball Quiz- 5pts
Vocab
- Turtle Programming - a classic method for learning programming with commands to control movement and drawing of an on-screen robot called a "turtle". The turtle hearkens back to early implementations in which children programmed a physical robot whose dome-like shape was reminiscent of a turtle.
- Algorithm - A precise sequence of instructions for processes that can be executed by a computer
- Iterate - To repeat in order to achieve, or get closer to, a desired goal.
- Selection - A generic term for a type of programming statement (usually an if-statement) that uses a Boolean condition to determine, or select, whether or not to run a certain block of statements.
- Boolean Condition- Using Boolean expressions (true/false) inside conditionals (if/else). Thanks to conditionals, programs can respond differently based on different inputs and parameters.
- Conditionals- programming element that allows a computer to make decisions depending on specific criteria. They enable a program to execute distinct code branches based on particular conditions.
- Sequencing - Putting commands in correct order so computers can read the commands.
- Abstraction: a simplified representation of something more complex. Abstractions allow you to hide details to help you manage complexity, focus on relevant concepts, and reason about problems at a higher level.
- Function: a named group of programming instructions. Functions are reusable abstractions that reduce the complexity of writing and maintaining programs
--Lesson 4--
- Video- Turtle Programming (4min)
- Learn to use the App Lab programming environment
- Write a program that uses basic "building blocks" to draw an image in App Lab
- Think about what "efficiency" means when programming
Complete Lesson 4
--Lesson 5--
- Video- Calling Functions (5min)
- Define and Call Functions (Proceedures)
- Write functions with names that describe what each function does in solving the problem.
- Write a program that uses more than one function and more than one level of abstraction.
Complete Lesson 5
Introduced Code
New Blocks
Next Week-
- LEGO Written Program
- More Turtle Programming
- Group Turtle Picture Drawing
Sign-Up for AP Test- You will do great!
|
Week 11 |

Day 23- Monday October 16- Data Breaches / Cyber Attacks / Passwords
- No Quiz Today / Substitute today
- My dad is in hospital, so I am with him today
- 3 Topics today, Quiz Wednesday, and Test Friday
- Use headphones or Closed Coptions for your 2 videos today
- Sign-Up for AP Test- You will do great!
Hacks and Attacks-
- Video- The Internet: Cybersecurity & Crime
- Keylogging- The use of a computer program to record every keystroke made by a computer user, especially in order to gain fraudulent access to passwords and other confidential information.
- Phishing- The fraudulent practice of sending emails purporting to be from reputable companies in order to induce individuals to reveal personal information, such as passwords and credit card numbers.
- Malware- Malware (short for “malicious software”) is a file or code, typically delivered over a network, that infects, explores, steals or conducts virtually any behavior an attacker wants. And because malware comes in so many variants, there are numerous methods to infect computer systems.
- Ransomware- Ransomware is a malware designed to deny a user or organization access to files on their computer. By encrypting these files and demanding a ransom payment for the decryption key, cyberattackers place organizations in a position where paying the ransom is the easiest and cheapest way to regain access to their files.
Passwords-
Data Breaches-
- Use this Website- World's Biggest Data Breaches & Hacks
- Pick a Data Breach and research it some more
- Make a 7 page Google Slides presentation including and of the following Info (5pts)
- Share with Coach B
- Link to at least 2 articles about your Data Breach
- List date, time, and company name of the Data Breach
- What was taken in the Data Breach
- What was the cost of the breach
- Could it have been avoided
- Was there any ransom paid
- Were customers effected in anyway
- Did the company lose any business
- Is the company doing anything now to include more data security
- Anything else we should know
Journal Love (Quiz Wednesday 10pts, Test Friday 40pts)
- Vocab- Cyber Army, cybercrime, Keylogging, Phishing, Malware, Ransomeware, Virus, DDoS, Hacker, BotNet
- Password Tips
- Solariwnds
- Data Breaches and Hacks
Sign-Up for AP Test- You will do great!

Day 24- Wednesday October 18- Burrill / Encryption
Coach Burrill Footprint Day
Encryption and Data Protection
Sign-Up for AP Test- You will do great!

Day 25- Friday October 20
|
Week 10 |

Day 21- Tuesday October 10
No Quiz Today
AI-
- Since its beginning, artificial intelligence has come under scrutiny from scientists and the public alike. One common theme is the idea that machines will become so highly developed that humans will not be able to keep up and they will take off on their own, redesigning themselves at an exponential rate.
- Weak artificial intelligence embodies a system designed to carry out one particular job. Weak AI systems include video games such as the chess example from above and personal assistants such as Amazon's Alexa and Apple's Siri. You ask the assistant a question, and it answers it for you.
- Strong artificial intelligence systems are systems that carry on the tasks considered to be human-like. These tend to be more complex and complicated systems. They are programmed to handle situations in which they may be required to problem solve without having a person intervene. These kinds of systems can be found in applications like self-driving cars or in hospital operating rooms.
Watson!-
- Video- Supercomputer: Watson(IBM computing system) - Documentary [HD]
- Machine Learning- is a method of data analysis that automates analytical model building. It is a branch of artificial intelligence based on the idea that systems can learn from data, identify patterns and make decisions with minimal human intervention.
- Bias- Machine Learning bias, also known as algorithm bias or Artificial Intelligence bias, refers to the tendency of algorithms to reflect human biases. It is a phenomenon that arises when an algorithm delivers systematically biased results as a consequence of erroneous assumptions of the Machine Learning process Examples- Race, Gender, Economic, Religion, etc…
- What is inside Watson- a cluster of ninety IBM Power 750 servers, each of which uses a 3.5 GHz POWER7 eight-core processor, with four threads per core. In total, the system has 2,880 POWER7 processor threads and 16 terabytes of RAM.
- Video- Watson and the Jeopardy! Challenge
- What is Watson being used for now- Weather Forecasting, Building Codes, Cancer Treatment, Financial Planning, Teaching Assistance Tools, Tax Preparation, Fashinon Design, and Advertising.
- Discuss Videos
Complete code.org Unit 5 Lesson 6
Day 22- Thursday October 12
Big Data-
Privacy Policies-
Video- How to read privacy policies like a lawyer
- Discuss Video
- Pick a App/Website to Look at Privacy Policy - Ideas Below
- Education: Code.org, Khan Academy, Codecademy.com
- Social media: Facebook, Twitter, Instagram, Snapchat, Tik Tok
- Online store: Amazon, Target, Walmart
- Mail & communication: Gmail, Hotmail, Yahoo Mail, Skype, Google Hangouts
- Streaming sites: Netflix, Spotify, Pandora
- Gaming sites: Steam, Xbox Live
- 3pts- Create a One Page Document listing thoughts about Google Privacy & Terms of Usage (1-3 People)
Facial Recognition-
- Video- Is Facial Recognition Invading Your Privacy?
- Do the harms of giving up privacy outweigh the benefits of the technology they power.
- Key Takeaways
- Data that may not seem private, like a birthdate or zipcode, can be combined to uniquely identify you.
- Personally Identifiable Information (PII): information about an individual that identifies, links, relates, or describes them.
- Technology enables the collection, use, and exploitation of information about, by and for individuals, groups, and institutions. Geolocation, cookies, and browsing history can all be used to create knowledge about an individual. Most digital technology needs some kind of PII to work (for example street navigation needs to know your location or PII stored online to simplify making online purchases).
- Other times websites collect more data to improve their services.
- Many services and websites collect information (like your browser history) that can be used to advertise to you by creating detailed profiles of who you are and what you like. Search engines also can record and maintain a history of searches made by users. This information can be used to suggest websites or for for targeted marketing.
- Once data is made digital, and especially once it's shared online, it's much harder to control.
- PII can be used to steal the identity of a person, or stalk them online. Information that is often posted on social media can be combined to create a profile on you.
- Journal Love
|
Week 9 |

Day 19- Wednesday October 4

Day 20- Friday October 6
- Google and Amazon Quiz today- 10pts
- Enroll in College Board Class
- Follow directions on Website
- Use correct class code
- Apple Inc
- 1-3 Group- Big Data Project (5pts)
- Define and Explain the following 3 Data Topics-
- Big Data
- Open Data
- Crowdsourced Data
- Share your Google Doc with me
- Due at end of class
|
Week 8 |

Day 16- Monday September 25
- As promised for those 20% of you who will have a life altering experience...
- Review- The cinematography rivals that of Kubrick and Hitchcock. The animation is the best I've ever seen, I mean, it's truly stunning. Avatar doesn't even hold a candle to to this. The voice is passionate and memorable. Plus, that ending is one of the most emotionally charged scenes put to film. This film is so entirely great I just can't even handle its majesty.
- Opening of the movie- For the first time in history people and machinery are working together, realizing a dream. A uniting force that knows no geographical boundaries. Without regard to race, creed or color. A new era where communication truly brings people together. This is the dawn of The Net.
- Video- Warriors of the Net (13min)
- Manuscrpipt
- Need some merch?
- Quiz from last class- 6pts
- Mr. B Review Game
- Test Wednesday- 40pts

Day 17- Wednesday September 27

Day 18- Friday September 29
Review Unit 1
- Code.org Unit 1 Assessment
- 1 Hour to Complete Project
- Burrill Google Form
- 1-3 Person Project
- Place everyone's name on the Google Doc/Slides
- Google Slides or Google Doc Shared W/ C Burrill
- Create a review guide for Unit 1 based upon the questions and answers
Unit 5 - Data ('23-'24)
In this unit learn how data analysis helps turn raw data into useful information about the world. Learn how to use data visualization to find patterns inside of data sets and learn how this data analysis process is being used in contexts like open data or machine learning to help make decisions or learn more about our world. In the unit project, you'll analyze a dataset of your choosing and present your findings.
Next Week-
- Google Trends
- Amazon
- Apple
|
Week 7 |
Day 14- Tuesday September 19
- Test Review Soon?!?!
- Quiz Today- 10pts
- Internet Delivery Options
- TCP and UDP
- Video- The Internet: Packets, Routing & Reliability
- Unit 2 Lesson 5 Internet Simulator
- Complete Unit 2 Lessons 1-5 Questions and checks for understanding
- Journal Love
- Vocab- Telegraphs,Telephone, Ethernet Cable, WiFi, Fiber Optic Cable, Starlink, Alphabet Lasers, IP Packets, Router, UDP, TCP, Fault Tolerant, Reliability, Redundancy, Cheapest Route, Dense Wave Division Multiplexing, Repeaters
- Names- Cyrus West Field, Elon Musk, Vint Cerf, Bob Kahn
Day 15- Thursday September 21
- Quiz Today- 6pts
- Video- The Internet: HTTP & HTML
- Discuss Video
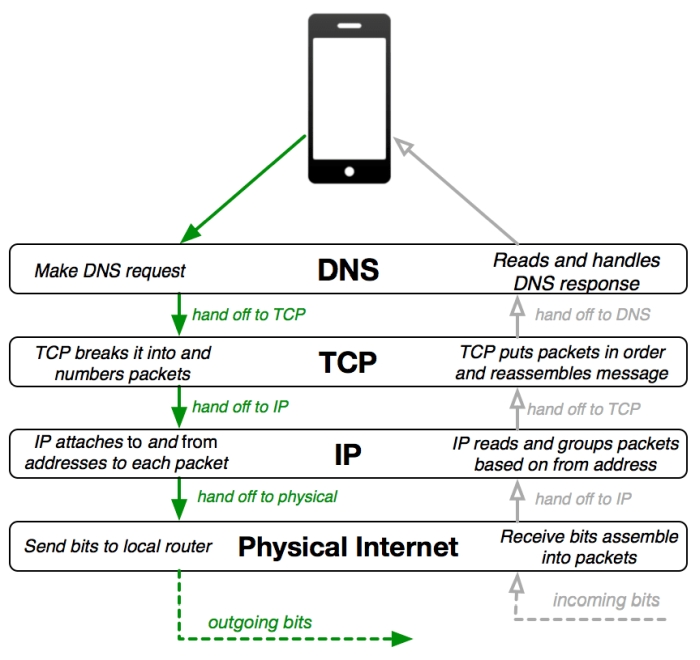
- Discuss Layers of the Internet (graphic above)
- Let's Make a Webpage in Dreamweaver and Look at the Code
- Vocab- HTTP, HTTPS, HTML, URL, Web Browser, Server, Get Request, Post Request, Cookie, SSL & TLS, Digital Certificate, Layers of the Internet, Dreamweaver
- Internet Simulator- Unit 1 Lesson 5
- Internet Simulator- Unit 1 Lesson 6
- Complete all of Unit 1 Code.org Lessons 1-7 (7pts, due on Wednesday)
- Warriors of the Net Video on Monday! Review Monday.
- Test Wednesday Next Week (40pts)
- Journal Love
|
Week 6 |

Day 11- Monday September 11
- Finish War Games movie
- A young computer whiz kid accidentally connects into a top secret super-computer which has complete control over the U.S. nuclear arsenal. It challenges him to a game between America and Russia, and he innocently starts the countdown to World War 3. Can he convince the computer he wanted to play a game and not the real thing
- Some Fun War Games Movie Facts/Info
- 1983 Release, Coach B is 13 years old and is in 8th grade.
- Movie made over $125 million at the U.S. box office.
- Cost $12 million to make the movie.
- It did cause some fear for Americans including then-President Ronald Reagan, who reportedly ordered a review on the security of defense computers after seeing the film.
- Movie was nominated for 3 Academy Awards.
- According to John Badham, the jeep trying to crash through the gate at NORAD and turning over was an actual accident. The jeep was supposed to continue through the gate. They added the scene of the characters running from the jeep and down the tunnel, and used the botched jeep stunt.
- The NORAD command center built for the movie cost $1 million, making it the most expensive set ever constructed at the time. The producers were not allowed into the actual NORAD command center, so they had to imagine what it was like. In the DVD commentary, director John Badham notes that the actual NORAD command center isn't nearly as elaborate as the one in the movie, calling the set "NORAD's wet dream of itself."
- The studio had the Galaxian (1979) and Galaga (1981) arcade machines delivered to Matthew Broderick's home. He practiced for two months to prepare for the arcade scene.
- The movie includes the first cinematic reference to a "firewall," a security measure used in computer networking and Internet security.
- The WOPR, as seen in the movie, was made of wood and painted with a metal-finish paint. As the crew filmed the displays of the WOPR, Special Effects Supervisor Michael L. Fink sat inside and entered information into an Apple II computer that drove the countdown display.
- 8 Question Quiz on War Games Movie (8 Pts)

Day 12- Wednesday September 13
- Unit 1 Test Review Soon?!?!
- Unit 2- Lesson 1
- After a short transition from representing information in Unit 1 to communicating information in Unit 2, students take time to think about their knowledge of the Internet and how it works. Following this, students are introduced to a new widget: The Internet Simulator which they will use throughout this unit to explore the inner workings of the Internet.
- The Internet
- The Internet Simulator
- What is the Internet?
- Explore the Internet Simulator. How does it work? What can I do with it?
- WWW
- Unit 2- Lesson 2- Computer Networks
- Computing Device: a machine that can run a program, including computers, tablets, servers, routers, and smart sensors
- Computing System: a group of computing devices and programs working together for a common purpose
- Computing Network: a group of interconnected computing devices capable of sending or receiving data.
- Path: the series of connections between computing devices on a network starting with a sender and ending with a receiver.
- Bandwidth: the maximum amount of data that can be sent in a fixed amount of time, usually measured in bits per second.
- Unit 2- Lesson 3-
- In a previous lesson, we explored the Internet Simulator, where each of you were connected to one other person by a single wire. What are the potential problems with this setup?
- Video 7min- The Internet IP Addresses and DNS
- A router is a networking device that forwards data packets between computer networks. Routers perform the traffic directing functions on the Internet. Data sent through the internet, such as a web page or email, is in the form of data packets. A packet is typically forwarded from one router to another router through the networks that constitute an internetwork (e.g. the Internet) until it reaches its destination node.
- Bandwidth: the maximum amount of data that can be sent in a fixed amount of time, usually measured in bits per second.
- Latency: Latency = delay. It’s the amount of delay (or time) it takes to send information from one point to the next. Latency is usually measured in milliseconds or ms. It’s also referred to (during speed tests) as a ping rate.
- Pipe Example- Bandwidth has to do with how wide or narrow a pipe is. Latency has to do with the contents of the pipe; how fast it moves from one end to the next.
- Internet Simulator Time- Unit 2. Lesson 3, Section 2
- Lots of Vocab- Protocols, Router, Bandwidth, Latency, Bit Rate, Inernet Protocol (IP), IP Addresses, ISP, IPv4, IPv6, DNS, DNS Spoofing, and DDoS
- All Together- Finish Code.org Unit 2, Lessons 1-3
- Journal Love
Day 13- Friday September 15
- Coach Burrill is absent today. His son is getting married tomorrow in Carlsbad!
- No quiz today, 10pt quiz on Tuesday next week covering first 2 days of Unit 2.
- Here is your work for today--
- 1-3 Students per group- No goups larger then 3!
- Make a Google Slides Presentation shared by each person in your group
- Share the Google Slides Presentation with me (Casey Burrill not Brady Burrill)
- Presentation must be at least 10 slides long (Title Slide is first slide)
- Make sure everyone's name is on the title slide
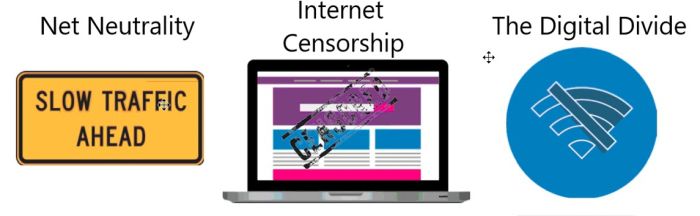
- Describe each of the 3 internet issues (Net Neutrality, Internet Censorship, and Digital Divide)
- Each internet issue should have 3 slides each
- Must have at least 3 images/graphs/pictures in your presentation for each internet issue
- Give an example of each internet issue
- List the issues in play for each of your examples
- Describe your groups feelings/opinions on the example you found
- Site your sources with a simple URL link to the webpage you found your information
- You have til the end of class to finish and share with Coach C Burrill
- When done with your Google Slides Presentation, you may work quietly til the end of the period
|
Week 5 |

Day 9- Tuesday September 5
- Creative Commons Quiz- 3pts
- World Famous Mr. B Review Game
- Journal/Notes Love

Day 10- Thursday September 5
- No Quiz today
- TAKE TEST TODAY!
- 40 pts
- 40 Multiple Choice Questions

- Start War Games movie
- A young computer whiz kid accidentally connects into a top secret super-computer which has complete control over the U.S. nuclear arsenal. It challenges him to a game between America and Russia, and he innocently starts the countdown to World War 3. Can he convince the computer he wanted to play a game and not the real thing
- Some Fun War Games Movie Facts/Info
- 1983 Release, Coach B is 13 years old and is in 8th grade.
- Movie made over $125 million at the U.S. box office.
- Cost $12 million to make the movie.
- It did cause some fear for Americans including then-President Ronald Reagan, who reportedly ordered a review on the security of defense computers after seeing the film.
- Movie was nominated for 3 Academy Awards.
- According to John Badham, the jeep trying to crash through the gate at NORAD and turning over was an actual accident. The jeep was supposed to continue through the gate. They added the scene of the characters running from the jeep and down the tunnel, and used the botched jeep stunt.
- The NORAD command center built for the movie cost $1 million, making it the most expensive set ever constructed at the time. The producers were not allowed into the actual NORAD command center, so they had to imagine what it was like. In the DVD commentary, director John Badham notes that the actual NORAD command center isn't nearly as elaborate as the one in the movie, calling the set "NORAD's wet dream of itself."
- The studio had the Galaxian (1979) and Galaga (1981) arcade machines delivered to Matthew Broderick's home. He practiced for two months to prepare for the arcade scene.
- The movie includes the first cinematic reference to a "firewall," a security measure used in computer networking and Internet security.
- The WOPR, as seen in the movie, was made of wood and painted with a metal-finish paint. As the crew filmed the displays of the WOPR, Special Effects Supervisor Michael L. Fink sat inside and entered information into an Apple II computer that drove the countdown display.
|
Week 4 |

Day 7- Tuesday August 29
- Quiz (5pts)- Hexadecimal/RGB
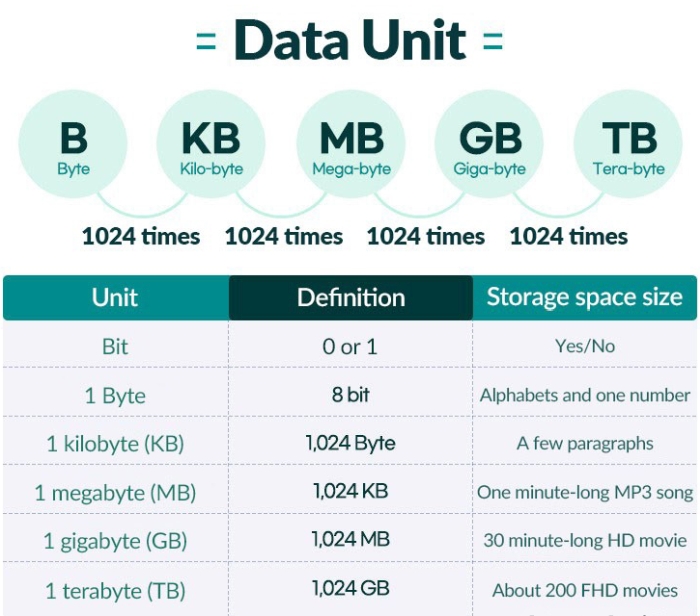
- File Size Discussion-
- Bytes, KB, MB, GB, TB, PB
- See Chart at bottom of today's schedule
- Lesson 9- Students use the Text Compression Widget to experiment with compressing songs and poems and try to find their ‘personal best’ compression. A video introduces important vocabulary for the lesson and demonstrates the full features of the widget. Students pick a text they think will be ‘easy’ to compress and one they think will be ‘difficult’, paying attention to why some texts might be more compressible than others. As a wrap-up, students discuss what factors make some texts more compressible than others.
- Lesson 10- Students are introduced to lossy compression via the Lossy Text Compression widget. They apply this concept and their prior knowledge of sampling to create their own lossy compressions of image files using the Lossy Image Widget. Students then discuss several practical scenarios where they need to decide whether to use a lossy or lossless compression algorithm. The lesson ends with a discussion of the situations where lossless compression is important and the situations where lossy compression is important.
- Using abbreviations and symbols is a form of compression, where we try to represent the same information with fewer characters.
- Video- Text compression widget with Aloe Blacc
- Use the Text Compression Widget to experiment with compressing songs and poems and try to find your ‘personal best’ compression.
- The widget we are using is an example of lossless compression
- The compression percentage at the bottom of the screen is calculated by comparing the number of bytes in the original message and the number of bytes in the compressed message.
- Complete Code.org Unit 1 Lesson 9 & 10- 3pts
- Journal Love

Day 8- Thursday August 31
- Quiz- Lossy/Lossless (5pts)
- Article- US Copyright Office: AI Generated Works Are Not Eligible for Copyright
- Today's Presentation
- Lesson 11- Students are asked to reflect on who owns their creative works from this class, such as their pixel images, before reading an article describing how ownership can become complicated as analog works become digital artifacts. After reading the article, students watch several videos explaining copyright and introducing them to the Creative Commons. Students then discuss the benefits, harms, and impacts of current copyright policy
- Lesson 12- In this lesson students begin tackling the question of whether digitizing information has made the world a better or worse place. Students then choose an article they are interested in reading. Students will discuss their preliminary reading and opinions after today's lesson and will have a chance to share with the class.
- Unit 1- Lesson 11-12
- Journal/Notes Love
- USC Plays Football Saturday, 3:30pm PST.
- Fight On!
|
Week 3 |
Monday August 21
School Cancelled!
Day 5- Wednesday August 23
Points today- Quiz (5pts), Code.org Unit 1 Lesson 7 (3pts), Activity Guide (5pts)
- Quiz- Binary/Text/ASCII (5pts), use your ASCII Chart (Open for first 10 minutes of class only)
- USC Plays Football on Saturday!

- Vocab- Analog, digital, metadata, pixel, and sample
- Watch Video on your monitor, turn on CC- Screen Histury Part 1 (2min)
- Students explore how black and white images are represented. Students use the black and white pixelation widget on code.org to represent each pixel of an image with black or white light. They learn how to sample an analog image using small squares of uniform size (each represented with a black or white value) and reflect on the pros and cons of choosing a smaller or larger square size when sampling.
- Pixel- Picture Element, smallest square on a screen
- Pixel- White or Black pixel for today
- 0 = Black (Light Off), 1=White (Light On)
- Analog, Digital, Metadata, and Sample
- Watch Video on your monitor, turn on CC- B&W Pixelation Tutorial (3min)
- With Friends, Complete Code.org Unit 1 Leeson 7 (3pts) Including Challenge A, B, & C
- Complete with a friend or two- U1L7 Black and White Images - Activity Guide (5pts), Print out Guide and give to me Wednesday. You can also do everything electronicly and email it to me. Put you and your friends names on the activity guide.
- What are we doing Wednesday? Color Images!
- Journal/Notes Love

Day 6- Friday August 25
- No Quiz today
- Collect Syllabus
- Collect Page 2 of B7W Images Activity (5pts)
- Color Pixels on Your Screen
- This is a second opportunity for students to interact with the Pixelation Widget, but this time they will work with color pixels. Students start off learning that each pixel uses red, green, and blue lights that can be turned on or off using bits. They will create more color variants using an increasing amount of bits per pixel, and apply their learning by approximating an analog color image using the widget.
- Hexadecimal Counting System Needed for Colors on Your Screen
- 1 Byte used for each of the 3 colors
- 256 red * 256green * 256 blue = 16,777,216 total colrs available
- Instagram Video (6min)- Images, Pixels, and RGB
- Vocab- Pixel, Resolution, Density, Filter, Function, RGB, Hexadecimal
- Video- Hex Code for Dummies
- Video Game- Flippy Bit And The Attack Of The Hexadecimals From Base 16
- Hexadecimal, Decimal, nd Binary Online Converter
- Complete Code.org Unit 1 Lesson 8 (Couple Videos to Watch, Uce Closed Captions)- 3pts
- Journal/Notes Love
- USC Plays Football Tomorrow!
- Fight On!
|
Week 2 |

Day 3- Tuesday August 14
- Binary Quiz- 5 pts
- Watch Video (8min)- How Gangnam Style Broke YouTube
- Discuss Video
- Overflow Error- An error that occurs when the computer attempts to handle a number that is too large for it. Every computer has a well-defined range of values that it can represent. If during execution of a program it arrives at a number outside this range, it will experience an overflow error.
- Read Article- Y2K Bug
- Discuss Article
- Fractions/Decimals in Binary
- Create all Possible Fractions in binary?
- Radix Point- The most commonly known example is the decimal point, named so for its use in base 10 notation. Similarly, "binary point" is used for base 2. In most English-speaking countries the radix point is usually a small dot (.), but this can vary as other languages can use different notation such as a comma (,) instead.
- Log-In code.org
- Complete code.org Pre-Survey
- Complete Code.org Unit 1, Lessons 4 & 5 (2pts)
- Syllabus Next Class
- Notes/Journal Love
- Bring in an ACII Chart Friday- Included on Chart Should be...
- Keyboard Buttons
- Decimals
- Binary
- Hexadecimal
01010101 01000011 01001100 01000001 00100000 01101001 01110011 00100000 01001100 01100001 01101101 01100101 00100001
Day 4- Thursday August 16
- Discuss Syllabus- Due Next Week (10pts)
- My PowerPoint For Today
- Overflow, Y2K, fractions in binary, Gagnum Style, Radix Point Quiz- 5pts
- We know how computers count using binary, but what about text, words, sentaces?
- Representing Text in Binary
- ASCII (American Standard Code for Information Interchange) is one of the most common character encoding standards.
- Originally developed from telegraphic codes, ASCII is now widely used in electronic communication for conveying text. As computers can only understand numbers, the ASCII code represents text (characters) with different numbers.
- This is how a computer ‘understands’ and shows text.
- The original ASCII is based on 128 characters. These are the 26 letters of the English alphabet (both in lower and upper cases); numbers from 0 to 9; and various punctuation marks. In the ASCII code, each of these characters are assigned a decimal number from 0 to 127. For example, the ASCII representation of upper case A is 65 and the lower case a is 97.
- Watch video (8min)- ASCII (Binary as Text)
- ASCII- Sample ASCII Chart

- Display a ASCII Chart on your device
- What does this say- 01010101 01010011 01000011
- Can you write your first name in Binary???
- My name (Casey) is in the graphic to the right -->
- Write in Binary- "Hello, I am ____. I am ____ years old."
- There are online converters (like this one) if you want to wimp out and cheat
- My T-Shirt Today
- Sending text messages is an example of abstraction. For a computer, each character is a number value, which itself is really a binary number. It all comes back to zeroes and ones, always! Binary is KING!!!
- ASCII Art
- Binary Games
- Complete Code.org Unit 1 Lesson 6
- Journal/Notes Love
- Syllabus Due next week (10pts)
|
Week 1 |

Day 1- Wednesday August 10- Intro and Coach B Quiz
- Inttoduction to Class
- World "Famous" Mr. Burrill Quiz
- Check-Out Website- wrwebheads.com
Day 2- Friday August 12- Representing Information / Binary Numbers
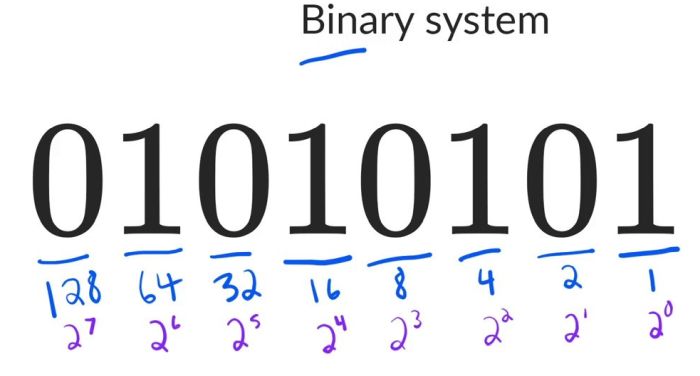
Binary Numbers-
In this lesson, students will practice representing numbers in binary (base 2). Students will create and use a "Flippy Do", a manipulative which helps students convert between binary (base 2) and decimal (base 10) numbers. They will practice converting numbers and explore the concept of place value in the context of binary numbers.
Take Away-
- Vocab- Bit, Byte, Transistor, CPU, Binary, Decimal, Hexadecimal
- Binary Counting
- Flippy Do Chart
- Join Code.org and Complete Pre-Course Survey
- Binary/Decimal Quiz on Tuesday next week. 5 Points
|
|










































